Just-in-Time Provisioning | Yext Hitchhikers Platform
Overview
Just-in-Time (JIT) provisioning is a way of automating user account creation for web applications. It uses SAML (Security Assertion Markup Language) to pass information from the identity provider to web applications. Meaning, when a new user tries to log in to an authorized app for the first time, they trigger the flow of information from the identity provider to the app that’s needed to create their account.
Just-in-Time SAML Provisioning
With Just-in-Time provisioning, you can use a SAML assertion to trigger the creation of a user the first time they try to log in to Yext with single sign-on (SSO). The process works as follows:
- In SAML responses, you can create an Attribute Statement containing the attributes needed to create a new user, including their name and information needed to grant them the correct access
- If a SAML login request is validated but refers to a user that does not yet exist in the account, a new user will be created, provided that sufficient attributes are supplied.
- If the user already exists, any attributes that are supplied are used to update the user (e.g., to update their name.) If any Access Control List entries are supplied, they completely replace the Access Control List entries the user currently has.
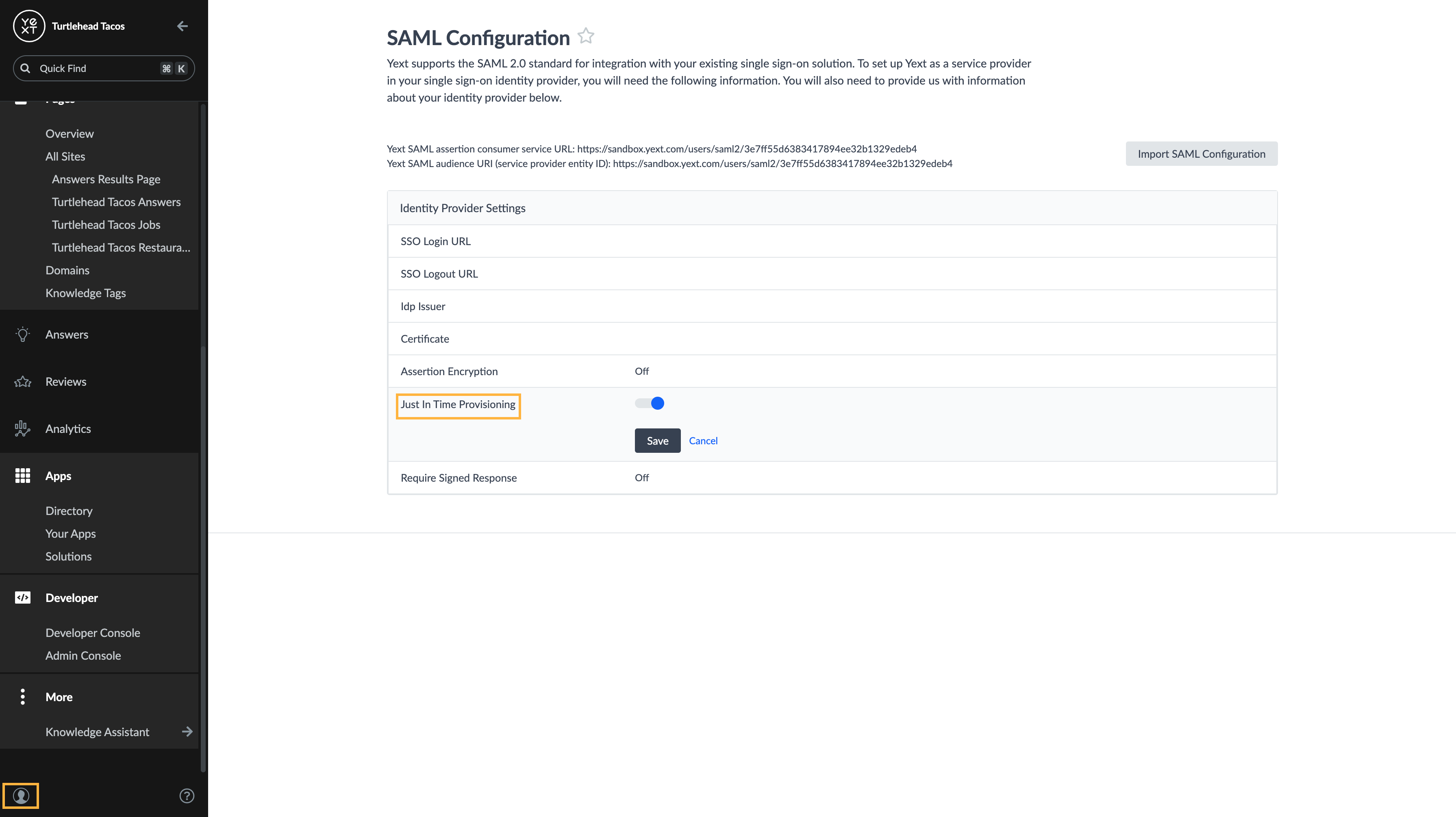
Turn on Just-in-Time Provisioning
- In your Yext account, click on the profile icon at the bottom of the navigation bar.
- Click Account Settings. From Account Settings, click SAML Configuration.
- Click on Just in Time Provisioning and select On. Then click Save.
Supported Attributes
The following attributes are supported:
| Attribute | Meaning |
|---|---|
firstName |
User’s first name |
lastName |
User’s last name |
emailAddress |
User’s email address |
phoneNumber |
User’s phone number |
acl[n].roleId |
Role ID for an ACL (Access Control List) entry that the user should be given (all other ACL entries will be cleared if the user exists). |
acl[n].on |
ID of the account, folder, or location that the ACL entry gives access to. |
acl[n].onType |
One of: ACCOUNT, FOLDER, LOCATION |
If any of the ACL attributes are supplied for a given n, they must all be. If a list of ACL entries is supplied, it is considered exhaustive and replaces the existing ACL entries for the user (unless they are the same).
This follows the pattern of the User object in the API , except that the following fields are not supported in JIT provisioning:
idusername– since that is in the NameID of the Subjectsso– always set totruewhen a user is successfully authenticated via SAML and JIT provisioning is on
SAML Response Format for Just-in-Time Provisioning
Attributes describing the user are supplied through a new AttributeStatement.
<samlp:Response ID="_257f9d9e9fa14962c0803903a6ccad931245264310738"
IssueInstant="2009-06-17T18:45:10.738Z" Version="2.0">
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">
lsmith@customer.net
</saml:NameID>
</saml:Subject>
<saml:AttributeStatement>
<saml:Attribute Name="firstName">
<saml:AttributeValue xsi:type="xs:anyType">Lucy</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="lastName">
<saml:AttributeValue xsi:type="xs:anyType">Smith</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="emailAddress">
<saml:AttributeValue xsi:type="xs:anyType">lsmith@customer.net</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="acl[0].roleId">
<saml:AttributeValue xsi:type="xs:anyType">43834</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="acl[0].on">
<saml:AttributeValue xsi:type="xs:anyType">349838474</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="acl[0].onType">
<saml:AttributeValue xsi:type="xs:anyType">ACCOUNT</saml:AttributeValue>
</saml:Attribute>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>
